A Honeypot Is Used for Which Purposet Tstout
Honeypot Front end interface. Up to 20 cash back Honeypots are also great training tools for technical security staff.

Types Of Honeypots Honeypot Is A Mechanism Used For Finding Hackers Before They Can Find And Attack Cyber Security Cyber Attack Computer System
Honeypots can also be weaponized.
. The reconnaissance task is the first and fundamental step an attacker does to proceed with a compromise. It is very easy to implement a honeypot. A honeypot is a controlled and safe environment for showing how attackers work and examining different types of threats.
A honeypot is a security resource whos value lies in. At a high level there are two main types of honeypot high interaction and low interaction. Use of so-called honeypots.
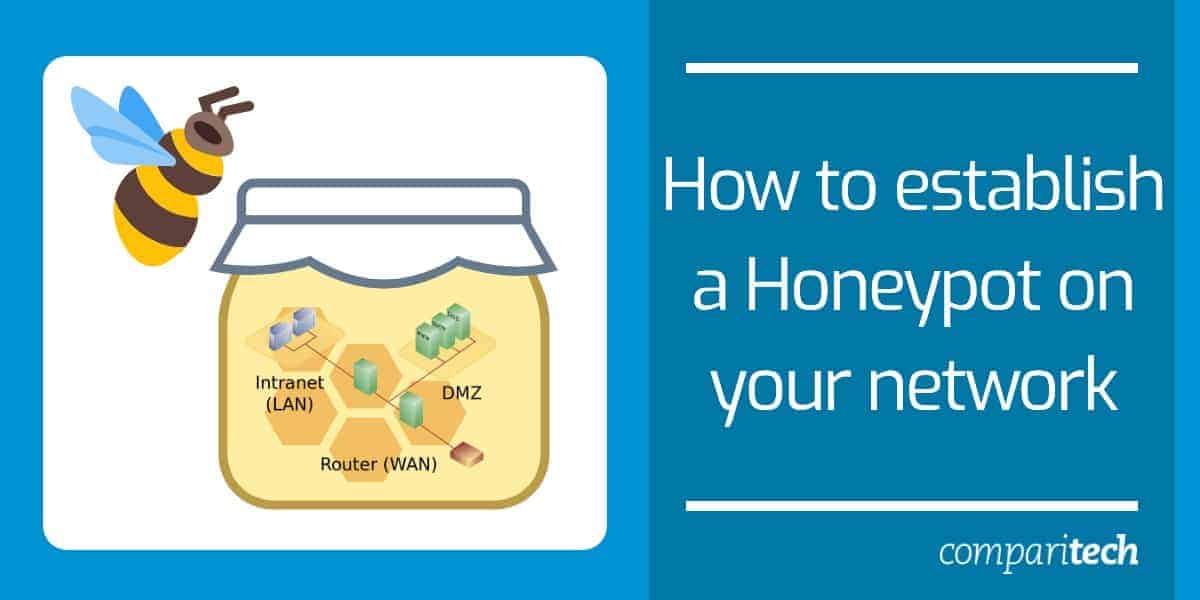
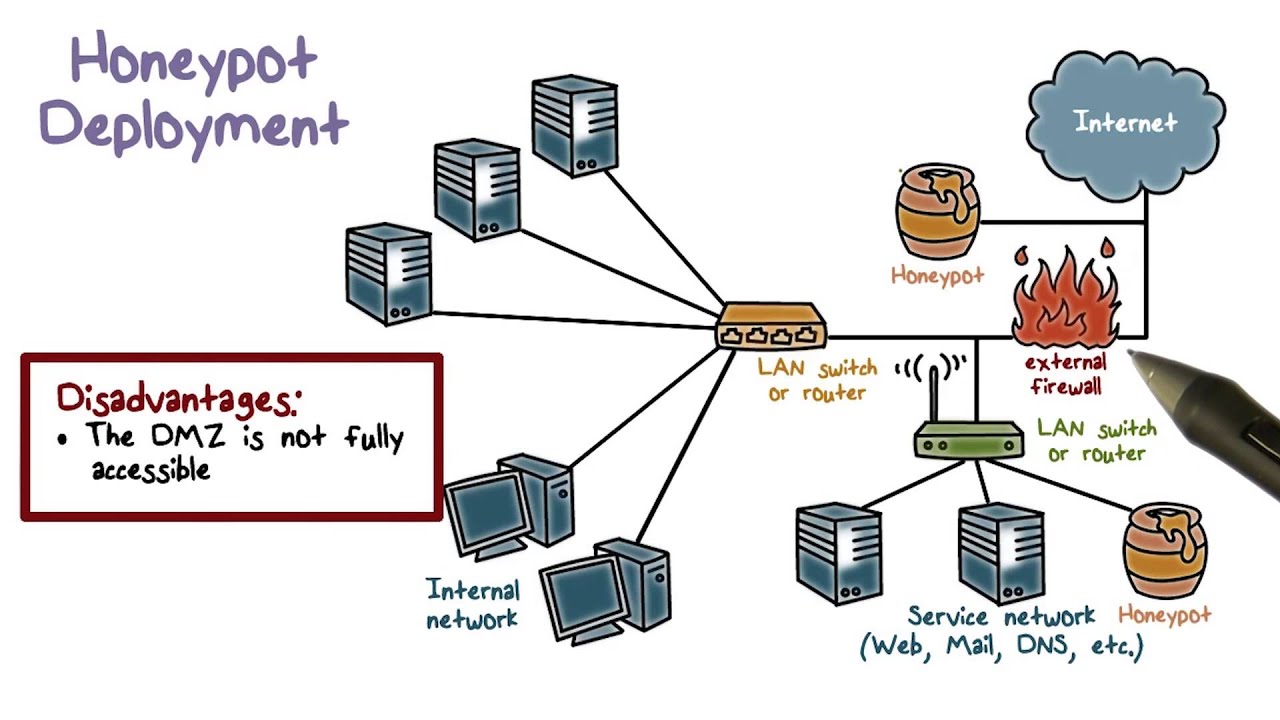
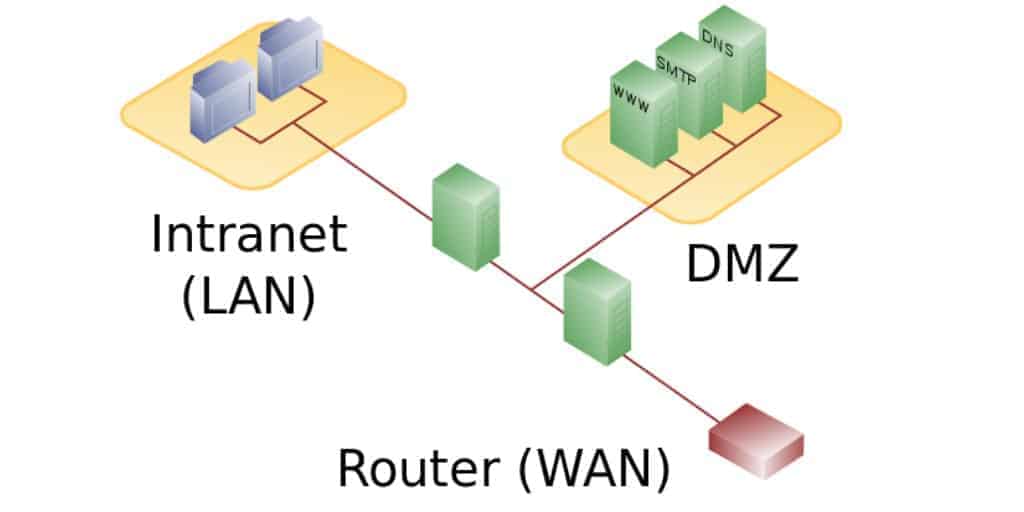
3 What is the typical configuration for a DMZ configured as a dual-homed gateway. A honeypot system can be deployed in a strategic network subnet mimicking a genuine host. A production honeypot is the most common type and used to gather intelligence information regarding cyberattacks within a production network.
If an internal host gets compromised and the host is used to do reconnaissance on the internal network this internal honeypot is a best system to identify these activities. A trap set specifically to lure hackers for the purpose of either catching them in the act or tracking them. By staging different types of vulnerabilities in the honeypot server you can analyze incoming types of attacks and malicious traffic patterns.
A honeypot is bait. A honeypot is used for which purpose. Additionally they can identify hackers with efficiency.
A honeypots purpose is to look like a legitimate network resource. Honeypots usually entice intruders to spend considerable time on the system and allow extensive logging of the intruders activities. Honeypots are mostly used by large companies and organizations involved in cybersecurity.
In computer terminology a honeypot is a computer system set to detect deflect or in some manner counteract attempts at unauthorized use of IT systems. Implementing a honeypot within a company can create a type of intrusion detection system. Modbus Honeypot implementation on SCADA infrastructure There are typically four components 1.
It can also be used to gain information about how cybercriminals operate. 2 How is a gateway different from a router. A honeypot is a fake network or system that hosts false information but responds as a real system should.
Honeypot systems use a dummy server to attract attacks. The honeypot is best known as a spy fiction concept. Honeypots are not only used for research purposes but also for production.
Modbus API module specifically implements the Modbus TCP protocol variant which is widely used in ICS Industrial Control Systems. Honeypots can emulate just about any server or PC based service you want them to from a fake MySQL database to an open file share or even a SCADA PLC. A honey pot is used for what purpose.
To entrap intruders To entrap intruders To delay intruders in order to gather auditing data To delay intruders in order to gather auditing data To prevent sensitive data from being accessed To prevent sensitive data from being accessed To disable an intruders system To disable an intruders system Explanation Explanation A honeypot is. There are three main different types of Honeypots categorized by their purpose and usage. 4 A screened subnet uses two firewalls.
The purpose of the honeypot approach is to distract attacks away from real network devices. It can be used to detect attacks or deflect them from a legitimate target. High interaction honeypots are normally used to study hacks in real time capture actions as they.
In essence it is a virtual sting operation. It acts as a potential target on the internet and informs the defenders about any unauthorized attempt to the information system. With a honeypot security staff wont be distracted by real traffic using the network - theyll be able to focus 100 on the threat.
A honeypot is a serverclient-based application that manipulates packets. You may not have heard of them before but honeypots have been around for decades. Honeypot is a network-attached system used as a trap for cyber-attackers to detect and study the tricks and types of attacks used by hackers.
TestOut Section 54 PowerPoints 1 How is a honeypot used to increase network security. A honeypot is used to delay intruders in order to gather auditing data. HUB To delay intruders in order to gather auditing data Crossover Ping.
Generally a honeypot appears to be part of a network but is actually isolated and monitored and which seems to contain information or a resource of value to attackers. A production honeypot can gather attributes like IP addresses data breach attempts. A honeypot is a computer or computer system intended to mimic likely targets of cyberattacks.
Its ease of operation and deployment makes it to use widely. A honeypot is a deliberately vulnerable target that invites penetration while fully instrumented. Generally the term refers to an alluring agent whose job is to draw the attention of the target.
A honeypot is a substitute for an IDS or firewall and protects a system. Generally it is an information system resource whose value lies in its unauthorized or illicit use by a hacker. The term honeypot has come to mean a deception technique to defend computer systems against malicious operations.
A honeypot is basically just a dummy network node software application or computer that exists for the sole purpose of getting hacked Figure 1. More precisely a honeypot is an information system resource whose value lies in monitoring unauthorized or illicit use of that resource.
How To Establish A Honeypot On Your Network Step By Step
0 Response to "A Honeypot Is Used for Which Purposet Tstout"
Post a Comment